Key Steps to Take When Operationalizing Cloud Governance
In today’s fast-paced world, it is easy to change a resource’s configuration in the cloud with one or two clicks. This allows you and your team to adapt to business needs and quickly test, integrate, and utilize new technologies. But the downside is limited visibility into ad hoc configuration changes and a lack of processes in place to respond appropriately. As a result, the cloud can quickly become an operational pain and increase security risks through unknown resource misconfigurations. To operate successfully in the cloud, you must have the people and processes in place that allow you to respond to changes in the cloud in near real-time. And you must also have the right technology in place that provides visibility into these changes and enables operational fitness and governance.
Before operationalizing cloud governance, there are a couple of prerequisites we need to examine. If you are just adopting the cloud, choose a project you would like to migrate and define the infrastructure Minimum Viable Product (MVP) you will need for that project.
Defining Gates & Guardrails
The first step is to define policy gates and guardrails you want to implement within your environment. Gates are placed in the environment around items that should be sectioned off with strict bounds. Guardrails are not as rigid as gates. For example, guardrails might conditionally allow access to parts of your infrastructure. Guardrails also assist with enhanced visibility around riskier parts of an environment. Gates and guardrails are implemented using the native policy management system, an example of which is Azure Resource Manager Policies. Examples of policies include: not deploying a storage account unless it is encrypted; or restricting certain expensive Virtual Machine sizes to contain costs.
Gates and guardrails (policies) are critical components of a successful cloud governance program. Azure, AWS, and GCP each have a native ability for you to create these policies. Preferably, you should deploy policies through Infrastructure as Code or using tools like Terraform. Most importantly, make sure you have clarity regarding of the all ways resources can be deployed, so changes to resources can’t sneak through policy enforcement points. This will help to ensure confidence in the environment’s security posture.
Adhering to Security Standards & Regulatory Compliance
Another important measure that must be taken is to plan how to monitor and evaluate your environment once the MVP is in place. If you have an established footprint in the cloud, and find your current cloud governance approach to be unscalable, you can follow these steps as well. You will simply be iterating your existing resource configuration right away.
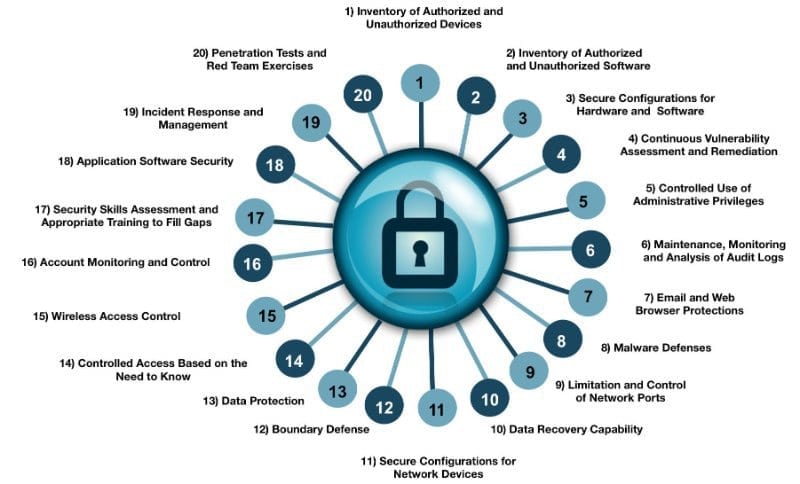
Automated evaluation against standards for both security and regulatory compliance is key. This allows governance to scale as your cloud infrastructure scales. First choose a security standard or regulatory compliance standard. We recommend the Center for Internet Security (CIS) and/or the National Institute of Standards and Technology’s Cyber Security Framework (NIST CSF) standards. These are the most common and foundational benchmarks that we currently see in use. The 20 CIS Controls and five NIST Functions are shown below. A key reason the CIS controls and NIST functions are used frequently in the cloud is because they are very prescriptive, particularly the CIS benchmarks. CIS benchmarks provide guidance on how to securely configure specific resource types in each of the major public clouds. We also see customers in more highly regulated industries evaluating their environments against NIST CSF and CIS compliance standards, due to the fact that many upstream regulatory bodies use these cloud security frameworks as a baseline.
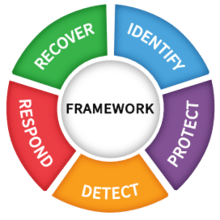 Source: NIST Cybersecurity Framework
Source: NIST Cybersecurity Framework
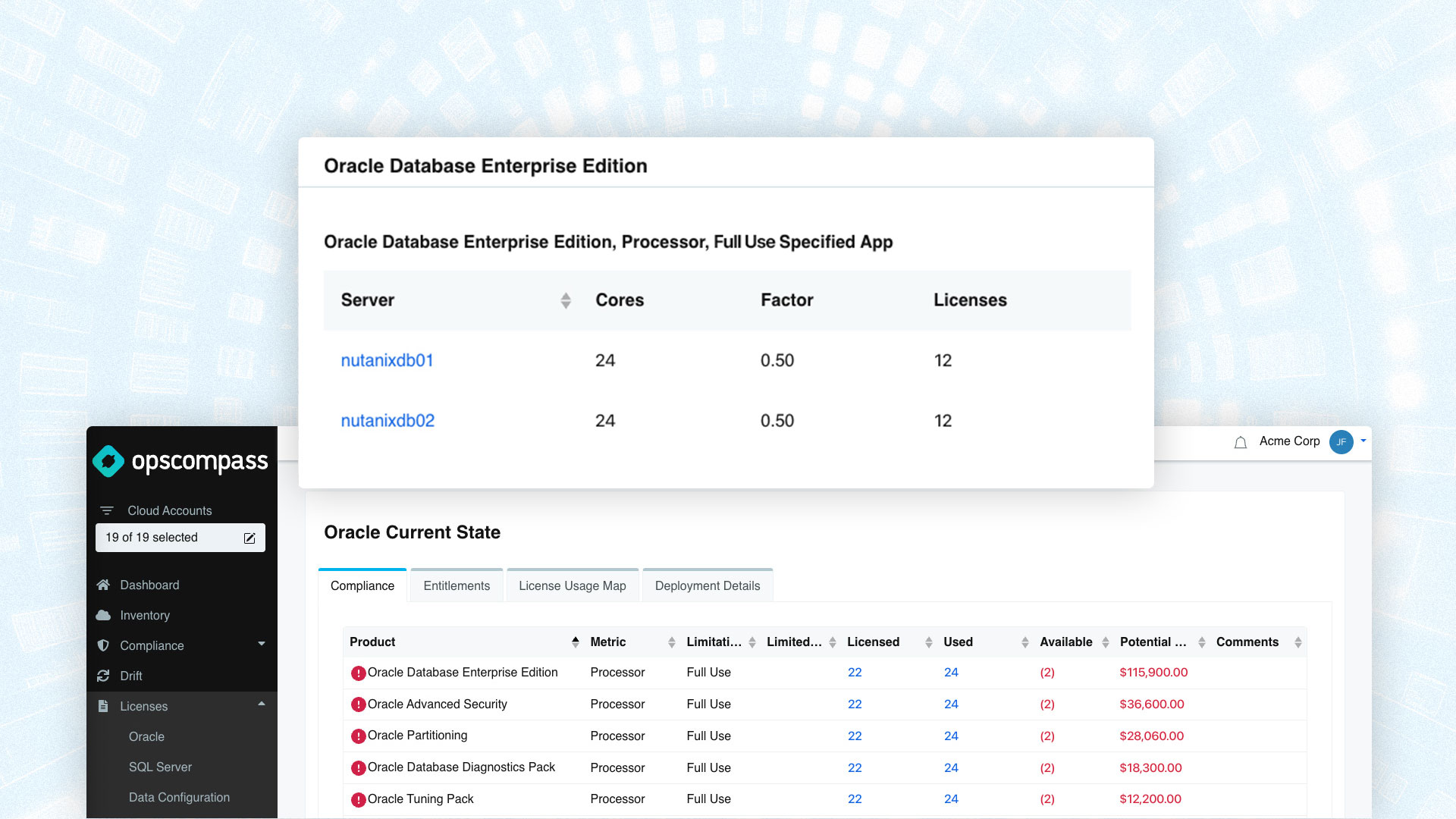
OpsCompass automates the evaluation of resources against CIS and NIST CSF benchmarks (as well as against regulatory compliance frameworks like PCI DSS, SOC TSP, HITRUST CSF, FedRAMP, and ISO 27001). Within 15 minutes of connecting a cloud account to OpsCompass, your resources are evaluated and displayed like those shown the image below. After initial set-up, resource creations, changes, and deletions are typically detected and evaluated within three minutes inside the cloud environment.
Whether you are just starting in the cloud, or are well established, CIS and/or NIST CSF allow you to specify a baseline for different resource type configurations from the start and scale from there. The frameworks (especially CIS) have specific actions and remediations that are defined, so operationalizing these actions and remediations into your day-to-day processes is a lot easier. They help you and your team focus time and energy on improving security posture, since you do not have to spend time reinventing the wheel for secure resource configurations.
CIS/NIST CSF establish a workable configuration baseline. As resources are provisioned, or if you are working through existing resources that are out of compliance, you can iterate back on the gates and guardrails that exist in your cloud. If your environment has several storage accounts, which are out of compliance with CIS because they are unencrypted, you can define a policy that requires all storage accounts have encryption enabled before deployment. Azure, AWS, and GCP all support the definition of similar policies.
Uncovering Configuration Drift
While some resource changes do not have an impact on the security framework baseline you have chosen for your environment, it is still important for you to monitor and review them. For example, you may accidentally assign an incorrect role to an identity group, which gives that group a higher level of permissions than intended. This type of change is resource configuration drift and needs to be reviewed. In our experience, the most successful cloud-first organizations review the previous day’s drift during their daily team standup and verify that all changes are expected changes. Automating drift detection allows these teams to spend their time reviewing the most critical information, rather than attempting to track it down across various cloud environments. Manually collecting this data is time-intensive and introduces the probability of human error.
OpsCompass automates drift detection and tags it with the appropriate impact for that change. This allows you to implement a process while ensuring the right people within your organization can quickly review that change.
Bringing People, Process, and Technology Together
To bring these plans and moving parts together, you need the right automated tool (technology) to provide the necessary visibility and compliance evaluation. Next, you need the right people in place to take the findings (of the automated tools) and act upon them. Finally, you need an iterative process to improve the gates and guardrails within your environment to increase the security posture of your cloud. Working configuration drift and compliance review into a daily standup, or other review meeting, enables continuous resource monitoring and iteration. This allows you to assess your environment quickly after a violation, instead of waiting until the next standard security review, which may be months away. Implementing these tools and teams helps enable a Cloud Center of Excellence. A Cloud Center of Excellence is a function that creates a balance between speed and stability. You do not want tools that cause more friction during this iterative process, rather you need tools that enable your team and become part of your operational process, so you can quickly react to changes that impact compliance.
The cloud brings Development, Security, and Operations more closely together than ever before. Operationalizing Cloud Governance helps to enable DevSecOps. This is where these teams work together into a single operational process. Collaboration is key, and a tool like OpsCompass helps these teams communicate and operate successfully in the cloud.
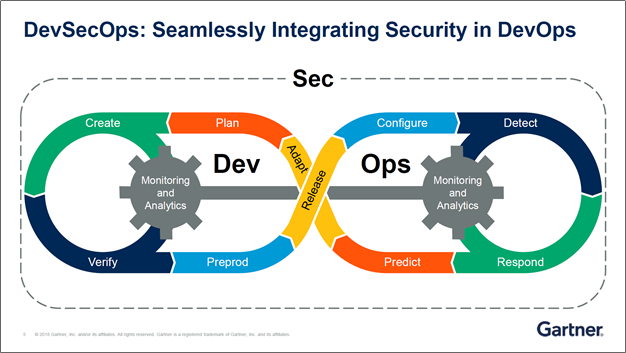
Source: Gartner, DevSecOps: How to Seamlessly Integrate Security Into DevOps, 30 September 2016, Ian Head, Neil MacDonald
Summary
OpsCompass helps operationalize cloud governance by automating evaluation of resource configurations against security standards and regulatory compliance, surfacing configuration drift, and facilitating seamless integration of people, process, and technology. To start operationalizing cloud governance in your Azure, AWS, GCP, and Microsoft 365 environments, sign up for a free trial.