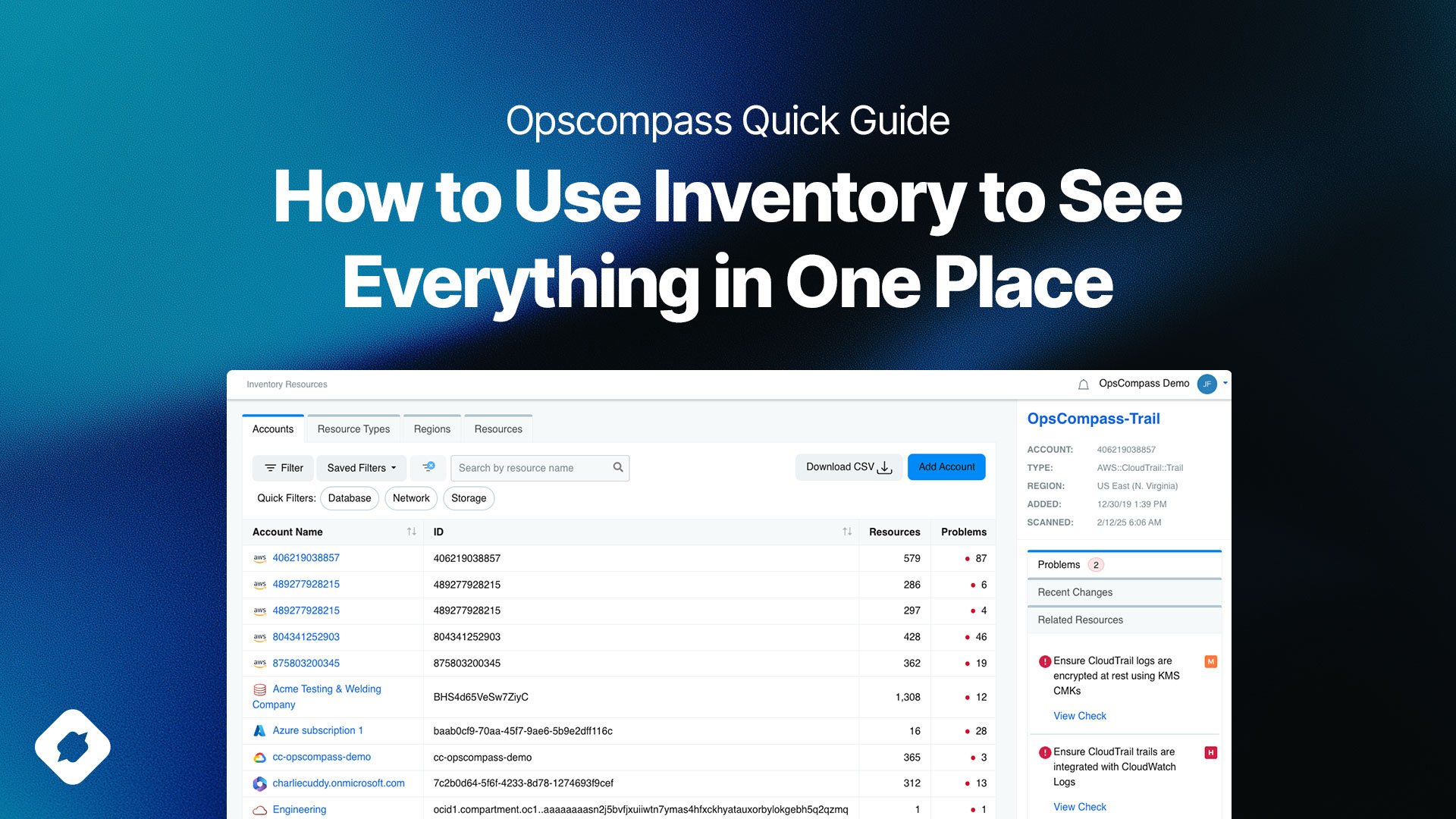
We spend a lot of time working with our customers to align their technology platform choices with best-practices security and compliance standards.
Over the past couple of years there has been a rash of high-profile data breaches and hack’s that have rocked the business world. At the same time there’s also been a veritable cambrian explosion of application frameworks, libraries, languages and database engines that are part of a new era of cloud-native applications – a direct response to mobile solidifying itself as the platform of the internet. With existential security risks for technology at an all-time high, and powerful cloud-native services popping up at a torrid pace, data security has never been more critical than it is today.
Having a fundamental knowledge of basic application environment security should be required for all of the members of your team. Whether dev or ops, everyone should understand the what it takes to keep your data protected. We thought it would be valuable to do a blog series of quick tips for securing your server environments and processes. Let’s start with a security fundamental that it is a requirement for nearly all of the main compliance standards: in-flight encryption.
All data that goes over your internal network or the internet is potentially vulnerable. Encrypting data in-flight means that you encrypt data when it’s being transmitted over a network.
Here are some tips to ensuring all of your data transmissions are encrypted in-flight:
- Don’t use ftp for file transfer, it’s unencrypted and insecure. Instead, use scp or sftp. Additionally, you can use rsync over ssh for secure transfer using rsync’s robust feature-set. On Windows you can transfer files over Remote Desktop which is also encrypted.
- On your web servers, whether you’re running on Windows or Linux, be sure to use TLS (transport layer security) for https on all of your connections.
- From time to time, a VPN is necessary to provide private, encrypted access to your network. We use OpenVPN as well as a hardware-based solution through our firewall. OpenVPN is software based, easy-to-use and is a great tool in your ops toolbox.
- When implementing encryption, try to avoid self-signed certificates wherever possible. It’s better to use a certificate that’s signed by a Certificate Authority and so your public key is always verified by a trusted third party.
These 4 tips are just the basics to encrypting your data in-flight. One challenge to implementing encryption is to ensure that it’s consistently implemented correctly across your entire environment as you grow. In our own infrastructure we’ve built encryption in-flight into our entire environment through our automation tools and we do quarterly audits of internal and customer environments. Security is a process that has to be taken seriously.
Next time we’ll touch on encryption at-rest and how to secure the data you’re actually storing.