Cloud adoption has led to a major shift in application security management. Unlike on-premises where the focus is more on perimeter security, cloud deployments demand a more holistic and integrated approach. Ensuring visibility into the security posture of your application components and identity framework, maintaining a baseline security configuration for all cloud resources, and enabling continuous monitoring to detect any changes are all essential steps in securing your applications in the cloud.
In face of evolving threats, this must be an ongoing process. It should start from the initial design phase, even before you’ve deployed your fist resource, and ideally should be integrated into the application lifecycle through DevSecOps.
In this blog post, we explore five best practices for securing workloads deployed in Azure, one of the most popular cloud platforms for SMBs and enterprises. We also discuss how real-time visibility of cloud resources and their configuration status can provide in-depth intelligence that is critical for cloud compliance.
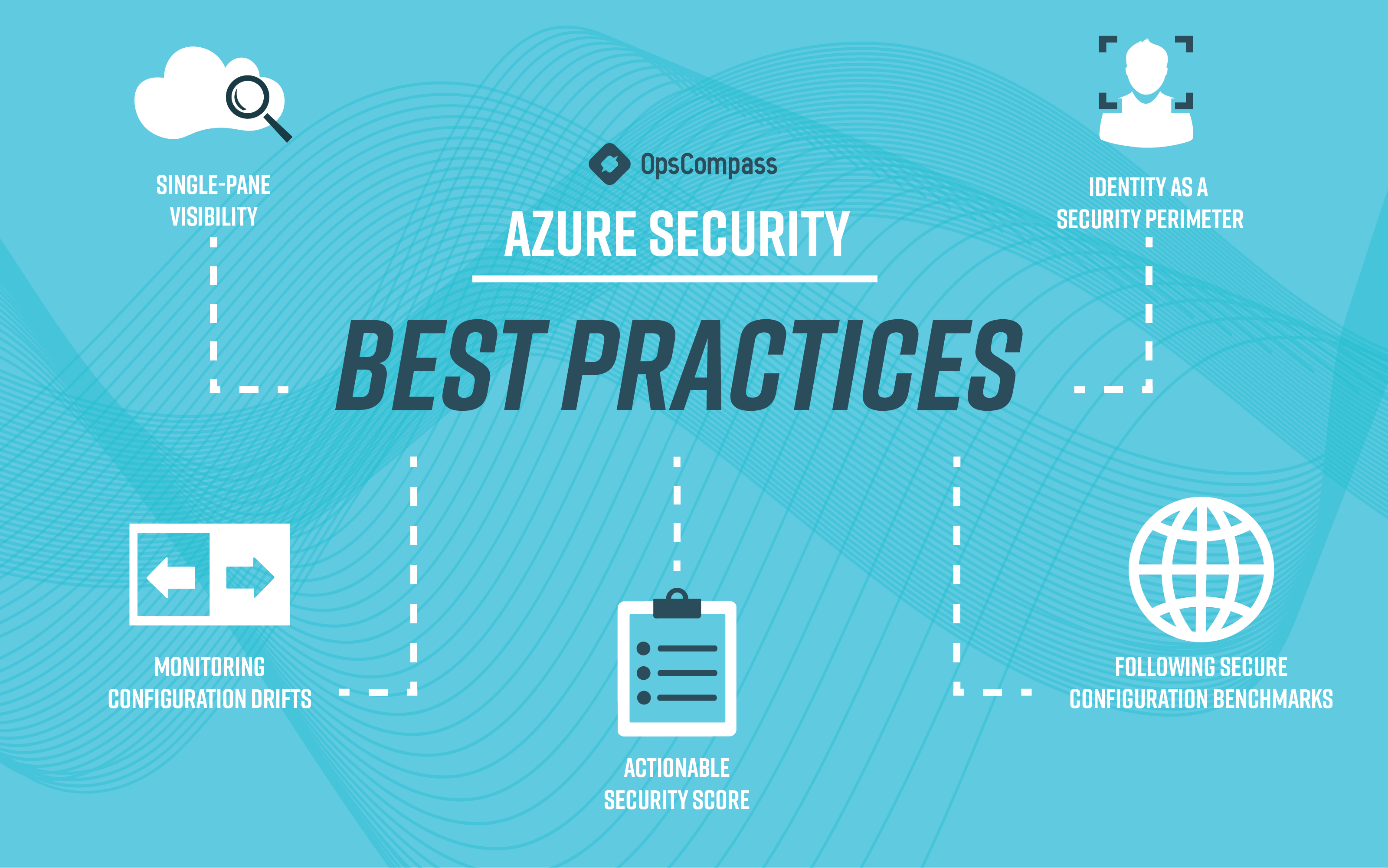
Azure Security Best Practices
Managing the security of numerous applications deployed across multiple cloud environments is complicated and can become a project in itself. But following the best practices discussed below can keep your applications safe in Azure with minimal effort. These include:
- Ensuring single-pane visibility into your Azure resources and managing their security posture.
- Enabling identity as a security perimeter to protect both your data plane and cloud-control plane.
- Leveraging tools that quantify your security posture through an actionable security score.
- Following the secure configuration benchmarks provided by frameworks like NIST and CIS to further enhance your cloud security posture.
- Monitoring your Azure resources for configuration drifts to prevent attackers from exploiting known vulnerabilities.
You can implement these security best practices through native services/tools in Azure, which can be augmented with third-party solutions as needed. Let’s review each of these security best practices more in depth.
1. Enabling Single-Pane Visibility
Azure advocates a layered defense-in-depth security approach in which necessary security controls are implemented from the infrastructure base layer all the way to application code. Single-pane visibility into your assets and their security status is critical here, as this provides a bird’s-eye view of your overall cloud security posture across these different layers. This allows you to identify weak spots in your environment and take corrective action.
The Azure Security Center onboards all resources through automated cloud asset discovery and provides a dashboard view of their security status. It also points out any loopholes and offers remediation recommendations for baseline security. This means cloud security teams don’t have to drill down to each and every resource independently to identify security flaws. With large and complex deployments, pinpointing issues can be particularly challenging. Azure Security Center provides single-pane visibility to address this.
Multicloud deployments, however, may still require cloud security posture management tools. These tools offer a unified view of all your resources and provide insights into the state of security across heterogeneous deployments.
2. Securing the Identity Perimeter
Azure uses role-based access control (RBAC) for control plane access, with users being granted administrative rights based on the assigned roles. By following the principle of least privilege (PoLP) users will only be given the minimum permissions required to execute authorized actions. In addition, you can restrict access for only the period of time required to complete the task with tools such as Just-in-Time (JIT) access for VMs or Shared Access Signature for storage. It’s also important to enable multi-factor authentication for all privileged users.
Securing the identity perimeter using a zero-trust approach is also essential as is continuously auditing access to resources to identify compromised identities and unruly insiders. In addition, logging usage of access rights across resources can help you identify unusual access patterns that could indicate an infiltration.
In addition to human identities, non-human identities in the cloud could also be accessing your resources and making configuration changes. These may include identities being used by DevOps tools. Azure AD audit logs help you keep track of user access activities such as provisioning and resource updates and flag any suspicious user sign-ins.
Last, tools that can identify and alert on insider threats and configuration drifts due to unauthorized access can help you take corrective actions.
3. Managing Security Posture
The more quantifiable your security posture is, the easier it will be to manage it. Azure Security Center assesses your resource security configurations against recommended baselines and provides a security score based on this. Once you’ve remediated the identified vulnerabilities, your security score should improve. This score-based approach classifies findings based on severity and allows you to prioritize critical recommendations. Some of the recommendations also come with auto-remediation options.
Multicloud deployments require single-pane management tools that are capable of evaluating configuration changes across different environments in order to provide a security score.
4. Adopting Secure Configuration Benchmarks
Depending on the the industry, organizations may be bound by compliance standards such as CIS, NIST, PCI DSS, and FedRAMPP for their cloud deployments. In such cases, you should conduct periodic security audits and publish the results to showcase compliance. This assures customers that their application and data are protected by controls defined by the compliance standards.
The Center for Internet Security (CIS) framework provides a set of controls and benchmarks with prescriptive guidelines for implementing cyber best practices and security hardening. The Microsoft Azure Foundations Benchmark version 1.2.0, widely adopted by leading organizations to ensure security in Azure, is the latest version of guidelines developed by a community of security practitioners and cyber experts.
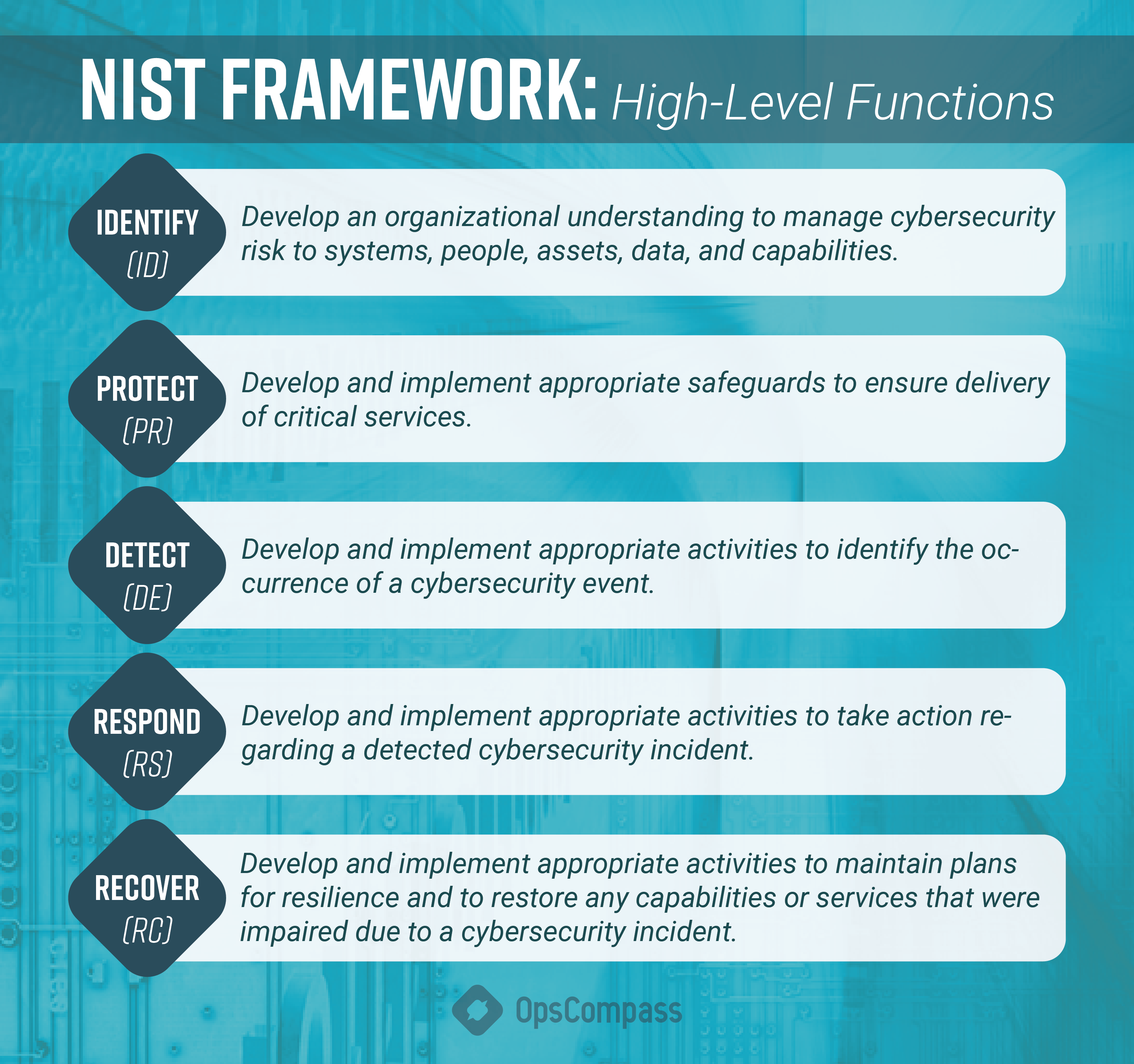
The NIST framework also provides guidelines for managing cybersecurity risks within organizations. Its core component outlines five high-level functions to achieve desired cybersecurity outcomes:
– Identify
– Protect
– Detect
– Respond
– Recover
As compliance requirements become more stringent, with new regulations being added regularly, ensuring compliance is becoming an increasingly complex task. There are, however, tools available that monitor your cloud assets against the compliance framework and provide a compliance score. These tools also offer automated assessment reports that identify controls your organization is missing and help fix them. Azure Security Center, for example, offers an out-of-the-box regulatory compliance score.
For multicloud deployments, you can take advantage of tools that provide a normalized score normalized score and consolidated dashboard that covers all your heterogeneous environments.
5. Avoiding Misconfigurations
Misconfigurations are one of the main issues that cause your cloud deployments to be vulnerable. Security should therefore be built in early in the development lifecycle by adopting a security-as-code approach through DevOps, in which security is baked into the code. This applies to both infrastructure as code (IaC) and application deployments.
Still, there is always the chance of human error. A Gartner cloud security report even predicted that through 2025, 99% of cloud security failures would be the customer’s fault. Regardless of whether the deployments are done manually or through Terraform, ARM template, CLI, or portal, keeping a close eye on configuration drifts and misconfigurations is key. You should ensure there are processes in place or tools at your disposal to continuously monitor your cloud configuration to allow for visibility and to identify possible risks. Mitigating them in time will prevent many security mishaps.
Visibility and Security in Multicloud
Nearly 81% of organizations are now considering a minimum of two public cloud service providers, according to Gartner. When it comes to multicloud, while the security best practices remain the same, one of the shortcomings of native security tools is that they are often more tailored for applications deployed on their respective cloud platforms.
OpsCompass provides a consistent approach to compliance and security across AWS, Azure, and GCP. It inspects your cloud resources and identifies risky configurations and configuration drifts. In addition, it evaluates your deployments against CIS and NIST standards and provides a proprietary compliance score. It also offers a single-pane view of configuration problem areas along with remediation recommendations.
OpsCompass gleans information from various sources both within and outside Azure to offer actionable insights. Unlike with native tools, you don’t have to go through multiple hops and views to get the information you need. OpsCompass ingests Azure Security Center recommendations and interfaces with native APIs, and all through a simple plug-in. This saves significant time and effort for multicloud deployments, in particular, which may otherwise have to be done manually.
Ensure visibility, derive intelligence, and control the security posture of your multicloud deployments. Sign up for a free trial of OpsCompass to streamline your cloud operations.