[et_pb_section fb_built=”1″ admin_label=”section” _builder_version=”3.22″][et_pb_row admin_label=”row” _builder_version=”3.25″ background_size=”initial” background_position=”top_left” background_repeat=”repeat”][et_pb_column type=”4_4″ _builder_version=”3.25″ custom_padding=”|||” custom_padding__hover=”|||”][et_pb_text admin_label=”Text” _builder_version=”4.9.4″ background_size=”initial” background_position=”top_left” background_repeat=”repeat”]
Managing and maintaining accurate baselines of your infrastructure across your entire cloud estate is absolutely crucial to a successful cloud governance program. Resource misconfiguration and drift are the leading causes of data breaches and cost overruns in the cloud – so much of the risk lies in your configurations. As your cloud footprint grows and more users are interacting with the environment, it’s important to monitor and track the exact configuration state of your applications, resources, and overall cloud platform.
In a traditional data center organization, one had to construct network maps, inventory spreadsheets, and accumulate information from disparate systems across their data center. But today the major cloud platforms are software oriented and built on unified sets of consistent API’s, meaning that it’s possible to get a complete view of your entire cloud presence. With this level of visibility and integration, cloud infrastructure baselines aren’t just possible, they’re central to DevSecOps collaboration and overall cloud governance.
What is a cloud baseline?
A cloud baseline is like a high-fidelity ‘snapshot’ of your entire cloud environment that is deemed to be a known-good state. This snapshot includes everything from the detailed settings of specific resources to identity and access. By having an accurate baseline, or a known-good state, you can then compare the current state of your cloud to the baseline to detect deviations. As your cloud environment grows and evolves – i.e. the configuration state of your cloud changes – maintaining and updating your cloud baselines becomes core to the governance process. With multiple clouds, potentially thousands of resources with varying configurations, and more users interacting with the environment, baselines become an indispensable way to know exactly what you have and how it’s changed.
Cloud baselines enable DevSecOps collaboration and accountability
Given the nature of agile development and automation in the cloud, changes happen more frequently, more people/teams are involved, and it’s the faster innovation that drives the business value. As your cloud environment quickly evolves and deviates from the baseline there should be processes in place to alert to these deviations and get the information about the change in front of the right teams. Those teams, or stakeholders to put it another way, should be accountable for changes and their impact. For example, if a SKU is upgraded on a service resulting in an increase in cost above a certain threshold you want the stakeholder to be aware and be able to maintain a cost baseline across your clouds. At the same time, that same SKU change could have compliance implications such as exposing the service to a network. As you can see, it’s critical that the compliance team gets alerted and is able to maintain a baseline of their compliance posture.
Maintaining cloud baselines forces development, security, and other stakeholders to be accountable for what gets deployed to the cloud. This collaboration combined with accountability is instrumental to success in the cloud.
Infrastructure-as-code is powerful but there are gaps
Infrastructure-as-code (IaC) tools are great to have in your DevOps toolbox. Popular IaC tools like Hashicorp’s Terraform, AWS CloudFormation, or Ansible are ubiquitous in cloud-enabled organizations. They help with the problem of resource consistency and drift, but these tools also have limitations and can give you an incomplete view. Companies often try to force all provisioning through IaC tools and even remove access to other methods. This approach is tempting as IaC tools are already necessary for DevOps automation and in an ideal world that would suffice. However, the fast moving cloud environments aren’t always ideal.
IaC tools don’t always support all of the available cloud platform resources so in those instances where you’re working with unsupported resource types your users will need another method for deployment, and you lose your ability to detect drift and changes. Also, IaC tools can tell you what they think is provisioned in your cloud, but they operate asynchronously, and you can’t know for sure without a centralized source of truth. Finally, with more users and potentially more autonomy extended to various stakeholders it’s difficult to guarantee that all of your users have the necessary expertise in your IaC tool of choice.
One of the best ways to thwart shadow IT and rogue cloud operations is to support multiple deployment methodologies across your enterprise and use cloud baselines to govern your environment.
Cloud baselines drive successful cloud governance
Developing discipline around cloud baselines allows organizations to fully leverage cloud agility and efficiency they’re looking for without sacrificing critical visibility and compliance. Companies can extend cloud autonomy (flexibility) down to business units or users allowing them to innovate flexibly with a variety of tools and resources, while staying in control and ensuring a certain configuration posture. Solid cloud governance means your stakeholders are part of a continuous, agile, collaborative process that makes them accountable for what get deployed out into your cloud and it’s impact.
Helm helps you get started with cloud baselines
Helm makes it easy to get started with cloud baselines right away and without the need for additional, highly trained staff. First, you want to start with best practices and consistency and expand from there. When you first setup Helm, it only takes a few minutes and you instantly have a CIS benchmark and a high fidelity snapshot of your entire environment. So with only a few clicks your cloud is baselined against an industry standard and Helm has a clear picture of your environment and all of it’s specific configurations. This is the start of your baseline!
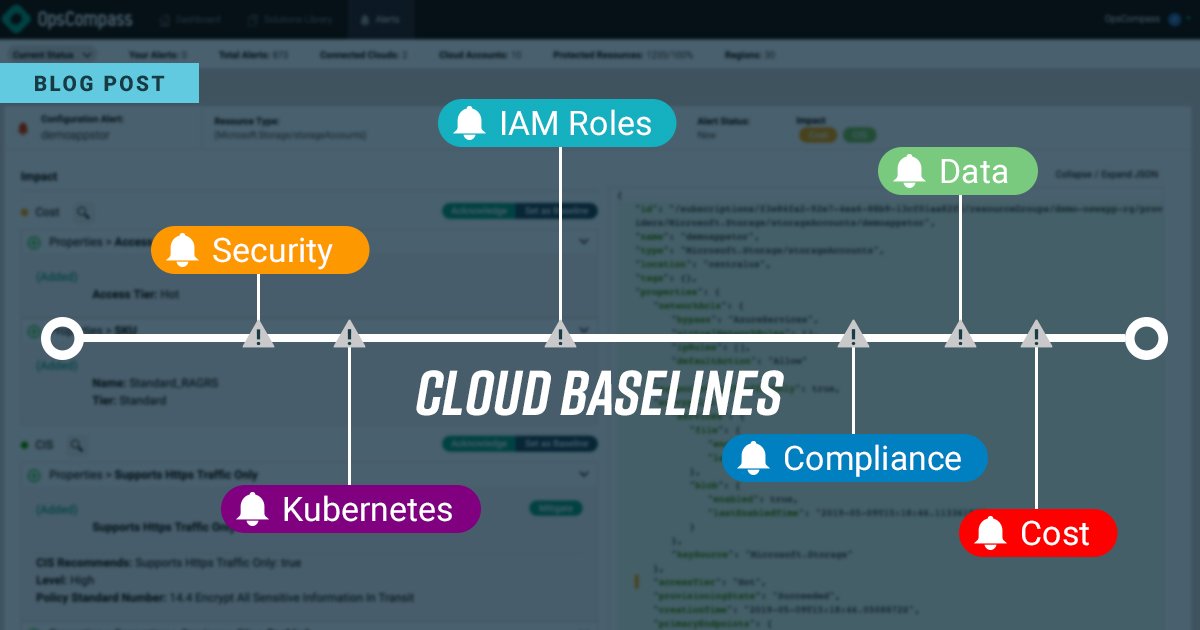
Now that your initial baseline is setup, Helm continuously inspects your environment and detects changes as they happen. These changes can be noisy, so Helm not only detects the change but determines it’s impact such as cost, security, and compliance and creates an alert.
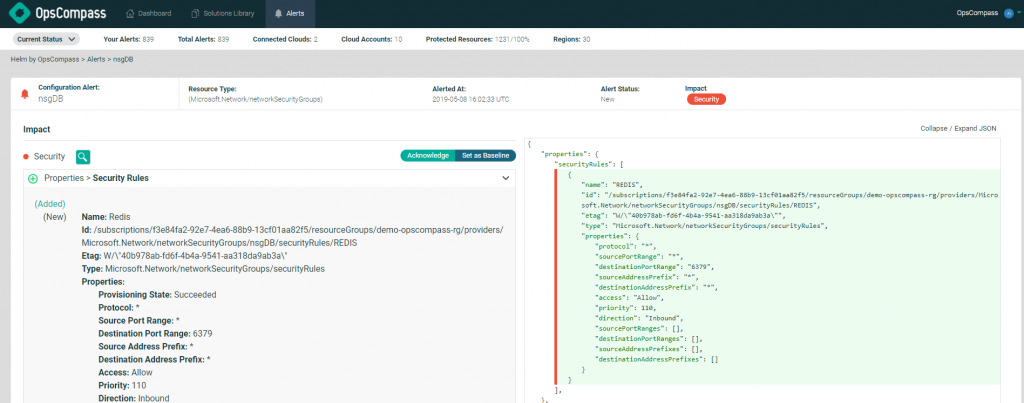
It’s important that these alerts get to the right people. You may have a person or team that’s concerned with cost and another that’s concerned with compliance or security. In Helm you can assign these concerns to different team’s and those team’s can maintain their own baselines. This creates a process of collaboration and accountability between stakeholders in your organization.

Helm baseline enforcement gives you a single source of truth for what actually got deployed in your cloud environment, how it’s different than your baseline, and the impact of that change. It’s all automated and continuous and integrates into your existing service management and ticketing systems.
If you’d like to check out all of this in action we’d love to schedule a demo with you today!
[/et_pb_text][/et_pb_column][/et_pb_row][/et_pb_section]