This article is part of our new State of Cloud Security 2021 Series which will interview a diverse mix of cloud security experts, design-makers, and practitioners with a goal of better understanding their perspectives on the current state of and future of cloud security.
The following is an interview OpsCompass CTO, John Grange recently had with John Verry, CISO and Managing Partner, Pivot Point Security.
JG: What is the state of cloud security today?
JV: It is great – until it isn’t.
Done “right”, migrating applications/servers/workloads to a mainstream Cloud Service Provider (CSP) increases the security posture of the average company. However, there is no “Easy button” to managing information security related risk, and truly achieving an improved security posture requires both an initial and ongoing commitment that most organizations do not fully understand or commit to. Unfortunately, that leaves them vulnerable to “cloud” security incidents (e.g., open S3 buckets) that are failures on their part, not the CSP.
JG: What are the most common challenges organizations face when it comes to cloud security today?
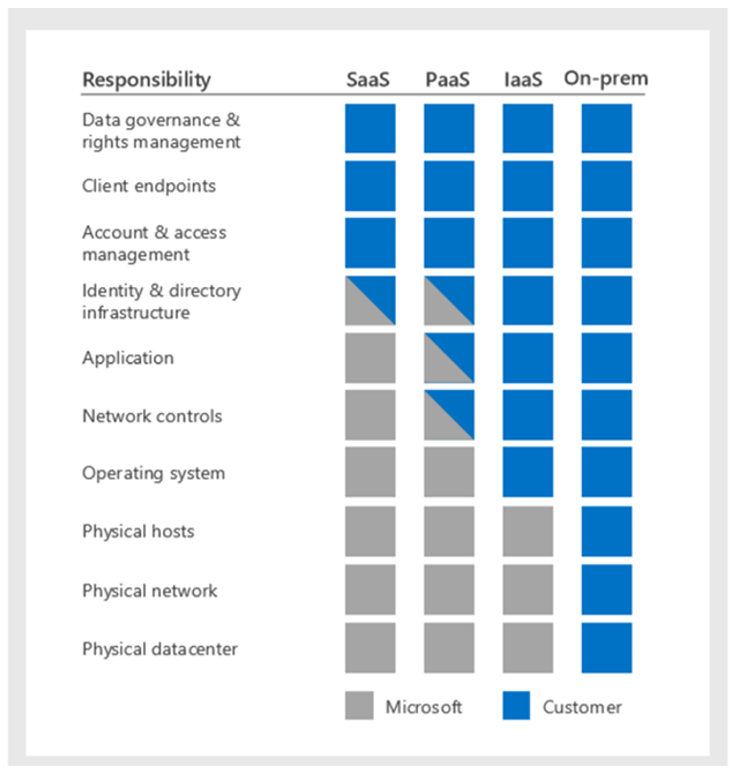
JV: The biggest concern is the mindset that security is the Cloud Service Providers responsibility. You can outsource a service (e.g., SaaS) to a CSP, but you cannot outsource the risk associated with that service. Ultimately, if your clients’ data ends up on the darknet, that is going to impact your organization way more than it will impact the CSP. To manage that risk, organizations must recognize that security is a “Shared Responsibility” for any service being acquired, and that they need to understand and execute on their end of the bargain. A good CSP will provide clear guidance (often referred to as “Rules of Behavior” or “Best Practices”) that outlines what they expect you to do from a security perspective to ensure the security of your data. This graphic illustrates what shared responsibility in the cloud looks like.
JG: What lessons can be learned from the biggest cloud-related breaches of 2020?
JV: What 2020 taught everyone is that we all need to plan for the unexpected. State sponsored attacks, a worldwide pandemic, software supply chain attacks, human error… In today’s world, building greater resilience into your cloud security is a must. For example, we encrypt all data before we store it in Microsoft 365, so if Microsoft is compromised our data will not be. I act as the Virtual CISO for a law firm that uses a cloud-based Document Management System to house all client matters. We host the encryption keys and generate an offsite copy of all of the files on a nightly basis, so a compromise and/or a ransomware attack against the CSP would have no impact on our client.
JG: What are 3-5 pieces of advice for organizations looking to improve their cloud security in 2021?
JV: Conduct a Risk Assessment on your use of the cloud. For those risks that are not acceptable, determine what you can do to reduce them to an acceptable level.
Understand your “Shared Responsibility”. Gap Assess what you are doing now against best practices for that cloud service. Put a plan in place to close those gaps. Ask questions like: What expertise are we lacking? What training do we need? What tools do we need?
Once you have a plan to be “compliant” with those best practices, figure out how you are going to monitor that compliance across each cloud service. Optimizing Microsoft 365 is arguably a full-time job for a subject matter expert. Add AWS, Azure, and a few others and having a single dashboard moves from a luxury to a necessity fast.
Ensure that your CSP contracts address their security requirements and that you have mechanisms in place to ensure that as your use of the service changes and/or the service changes those contractual obligations are updated.
Ensure that your CSP has clear requirements around returning data in a highly usable format should you need to terminate the contract. (We had a customer receive a mission critical database back as a single flat text file (relationality removed) that was essentially unusable).
JG: What is the future of cloud security?
JV: On the CSCP side, each breach drives greater scrutiny from regulators and potential clients, which will continue to accelerate their provable security/privacy/compliance efforts. The DoD’s CMMC model will have an immense impact as it rolls out across the Defense Industrial Base (DIB) and then more widely across other agencies, thus driving many CSPs to pursue a FedRAMP ATO to allow them to host data for CMMC Level 3 certified organizations. At the same time, most CSPs will need to address a quickly expanding set of Privacy requirements (APAC/GDPR/CCPA). Needless to say, this all comes at considerable cost. Hence, it is likely that there will be some consolidation in the CSP space as only the larger, more profitable CSPs will be able to afford the cost to achieve and maintain these certifications. A likely result is that there will be fewer breaches, but those that occur will be larger/more impactful.
On the consumer side, we will see a greater understanding of what “secure” use of the cloud requires. This will drive cloud-centric information security roles and better tools to identify and manage cloud-based assets across the diverse array of CSPs that most organizations use.