When people ask me what we do at OpsCompass, one of the things I say is, “We help you stay off the cover of The Wall Street Journal”. As I’m sure you’ve heard, Capital One has not had a good month in that regard. They recently had data on one hundred million customers stolen and shared publicly via data that was housed on the public cloud. There are a couple aspects to this breach that I want to highlight and how sound cloud governance plus OpsCompass can help with attacks of this nature.
What happened?
Here is the brief breakdown of what happened. The first step in the breach was using a Server Side Request Forgery (SSRF) attack. This specific weakness occurred inside the virtual machine Capital One was using as a Web Application Firewall (WAF). Then once they were able to get the credentials off the machine, they were able to use the same credentials of the virtual machine to list all the S3 buckets and then sync the contents of the S3 buckets to their local machine.
In the Well Architected Framework Security guidance, AWS makes it clear that security should be layered. So the failure was at three levels:
- The SSRF vulnerability.
- The WAF most likely did not need access to 14 years of credit applications and 140,00 social security numbers.
- The security policy should not have allowed access from outside the CapitalOne network.
AWS’s security guidance advises customers to take a layered approach to security so each of these issues should be addressed independently. I am going to focus on steps two and three and how following best practices, with a high leverage tool like OpsCompass, can help mitigate these problems.
The AWS Security Pillar states: “use detective controls to identify a potential security threat or incident. They are an essential part of governance frameworks and can be used to support a quality process, a legal or compliance obligation, and for threat identification and response efforts.”
Monitoring with OpsCompass
OpsCompass allows you to audit and review every change to your IAM roles and permissions. This gives you the capacity to review at a granular level that permissions are set correctly. In the screenshots of our SaaS platform, we’ve captured how our solution would capture an attack like the Capital One’s.
This first screen shows a real-time alert that there is change from a security baseline that was set by the cloud governance center of excellence team. We are monitoring Roles in this instance. Here we can see that our user interface is focusing precisely on the changes we have configured to monitor and we can see that a new policy has been added to our WAF role. An obvious question would be to ask why a WAF needs access to S3 and what buckets you can access through that role. Even with a strong change management process in place it is best practices to have critical changes reviewed by a third person. If this change were in error, malicious, or made outside of the standard change OpsCompass allows the appropriate personnel to quickly and easily review these changes.
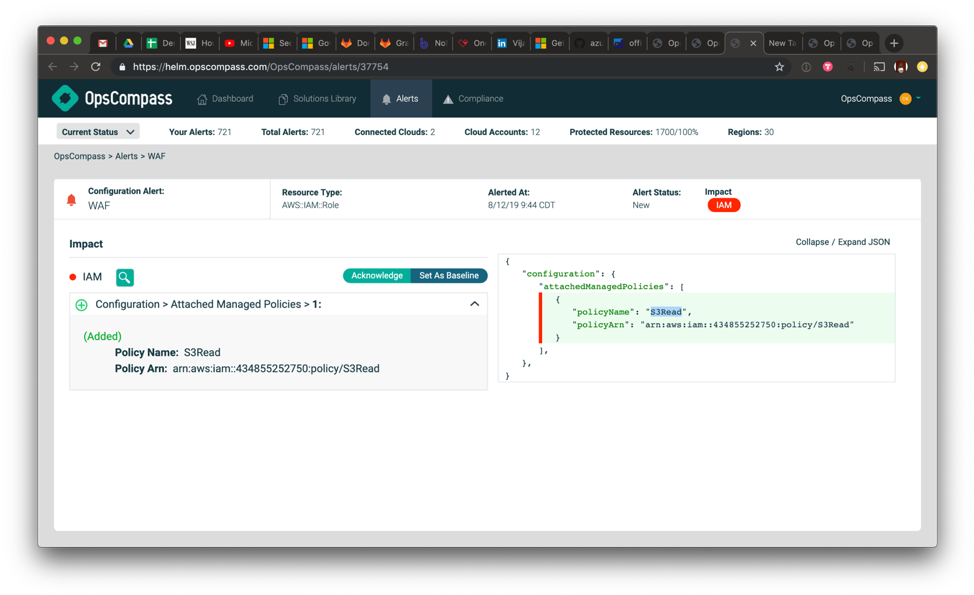
Real-time notifications
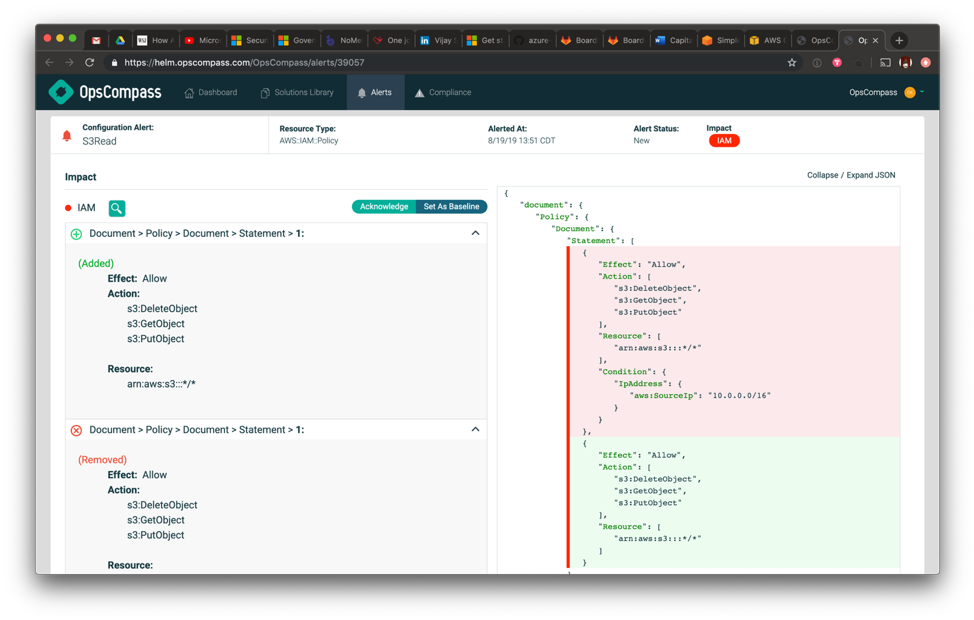
The next screen shows IP address restrictions being removed from a policy that enables users and instances to read and sync objects from S3 buckets. This is a red flag that either a mistake has been made or there is a bad actor involved. Again, by using our configurability for teams and concerns security team members see only the alerts they should review and can catch changes such as this one.
We can also create a custom compliance policy that will alert to all S3 related policies without IP restrictions allow you to define comprehensive rules for your security policies that can be evaluated quickly.
Conclusion
Unfortunately, these attacks will continue to rise, and we feel for those who manage and protect their organization’s most important data. There are too many positive benefits of the public cloud to stay on-premises. We want to make it easier and safer for you to bring your storage and workloads to Azure, AWS, or any other public platform. We understand your challenges and we look forward to helping you along your cloud journey.




