What is Configuration Drift and Why Does it Matter?
Understanding Cloud Configuration Drift
Organizations have been working to alleviate misconfigurations in their environments for as long as developers have been writing software. Unfortunately, configuration drift in the cloud is inevitable. Even companies with the best of intentions, who have worked through cloud adoption scenarios and based their infrastructure on well-architected frameworks, frequently run into changes from their baseline.
Configuration drift occurs when the actual known state of the infrastructure differs from the last defined configuration. There are a variety of reasons why this can happen, and the consequences of drift vary significantly – from simply being an annoyance to causing drastic failures in production.
Common Causes of Configuration Drift in Multi-Cloud Environments
Drift can occur by adding or removing resources or making changes to existing resource definitions. These changes can happen manually or via a number of automation tools.
- Changes in security settings, like opening unnecessary ports in a firewall
- Unintentional modifications to compute resources such as scaling VMs
- Configuration changes made outside of policy enforcement
- Cloud provider-initiated changes that affect existing configurations
The Hidden Risks of Unmanaged Configuration Changes
Configuration drift isn’t necessarily bad, but with the varying severity of consequences mixed with the speed of the cloud, awareness is vital. Without continuous drift monitoring, unintended misconfigurations can increase costs, impact security, and break compliance.
How Configuration Drift Impacts Cloud Security and Compliance
The Role of Configuration Drift in Cloud Misconfigurations
Even minor drift in cloud environments can result in exposed security vulnerabilities. For example, an open RDP port could be exploited, or excessive permissions could be granted unintentionally.
Compliance Challenges: CIS, NIST, and Other Security Benchmarks
Security and compliance frameworks like CIS, NIST CSF, and FedRAMP provide essential guidelines, but they cannot fully prevent configuration drift. Misconfigurations that don’t technically violate benchmarks can still introduce risk.
How Configuration Drift Contributes to Cloud Vulnerabilities
Drift can weaken identity and access management (IAM), expose unencrypted storage, or even impact regulatory compliance. Without proactive monitoring, organizations increase the likelihood of cloud breaches.
Maintaining Production Stability with Baseline Enforcement
Why Cloud Baselines Are Essential for Security and Compliance
A cloud baseline is a high-fidelity ‘snapshot’ of an environment deemed the known state. Maintaining an accurate baseline is a crucial step in cloud security and tracking configuration drift.
Automating Configuration Drift Detection for Proactive Risk Management
With cloud environments scaling dynamically, traditional tracking methods like spreadsheets are ineffective. Opscompass provides a continuous snapshot of each resource’s settings, offering real-time alerts for misconfigurations and drift.
Leveraging CSPM Tools to Strengthen Cloud Security Posture
While compliance frameworks help define security best practices, CSPM solutions like Opscompass take it a step further by continuously scanning for drift-related risks, ensuring that environments stay secure and optimized.
Improving Visibility with Frequent Cloud Audits
The Shared Responsibility Model: Who Owns Cloud Security?
Each cloud provider follows a shared responsibility model (AWS, Azure, GCP). Cloud providers are responsible for the security of the cloud, while enterprises must ensure security in the cloud. This includes protecting configurations, access policies, and infrastructure.
Conducting Regular Cloud Audits to Detect Misconfigurations
Regular internal cloud audits help organizations:
- Locate risks and misconfigurations
- Validate security and compliance policies
- Address vulnerabilities before they become major issues
How Opscompass Helps Maintain Continuous Compliance and Visibility
Opscompass offers any-time cloud audits that remain accurate with every change in the cloud. It highlights and categorizes configuration drift in real-time, ensuring that organizations stay ahead of compliance and security threats.
How to Identify and Manage Configuration Drift Effectively
Key Indicators of Configuration Drift in Cloud Infrastructure
Like a small leak behind a wall, configuration drift can go unnoticed until it causes major failures. Below are common drift scenarios that can significantly impact cloud operations.
Real-World Examples of Configuration Drift in AWS, Azure, and GCP
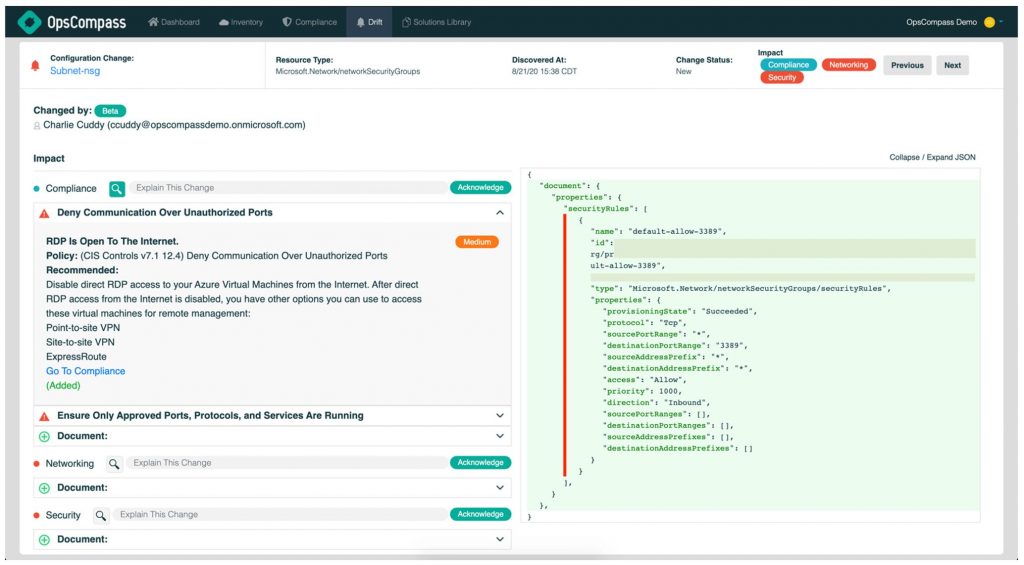
Firewall Rule Changes: A user opened RDP to the internet, increasing exposure to potential threats.
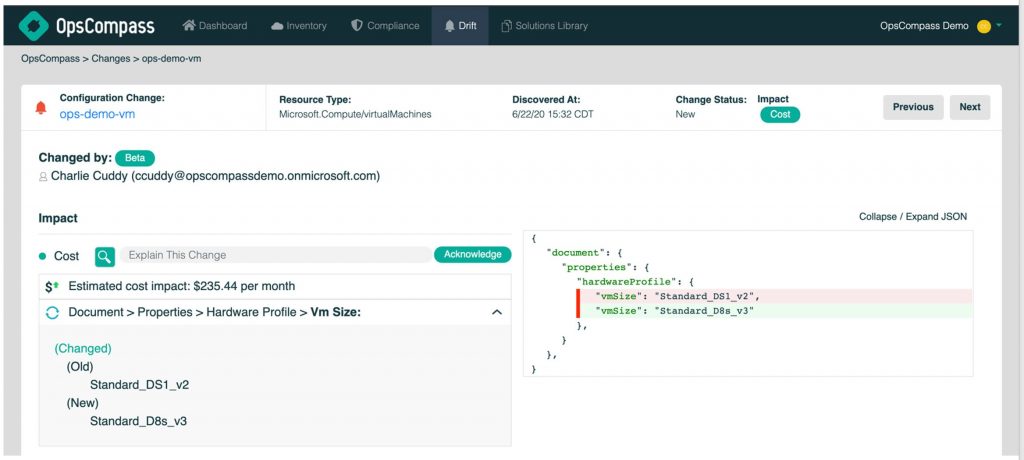
Virtual Machine Scaling: A VM’s SKU was changed, which increased cloud costs.
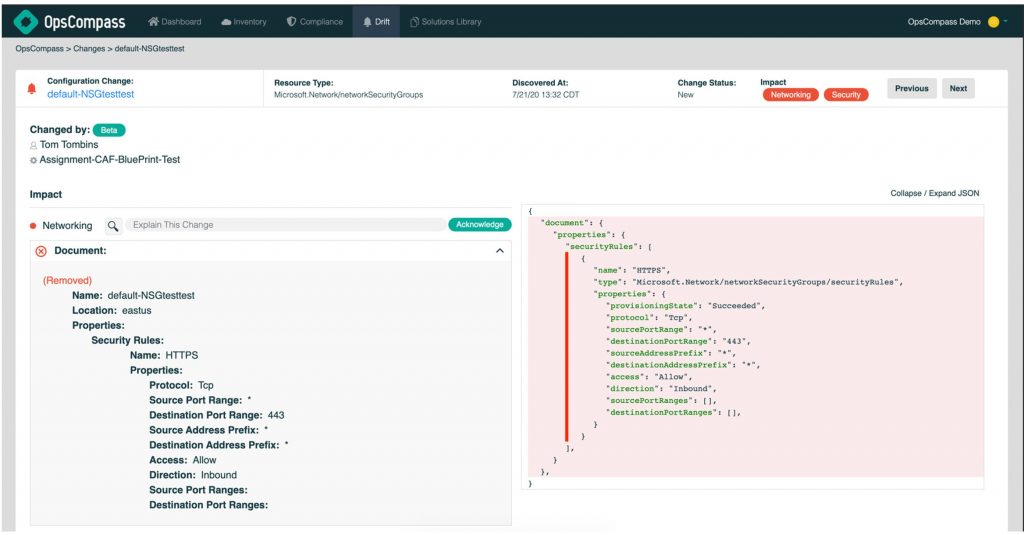
Security Group Modifications: HTTPS access was removed, leaving only HTTP, creating a security risk.
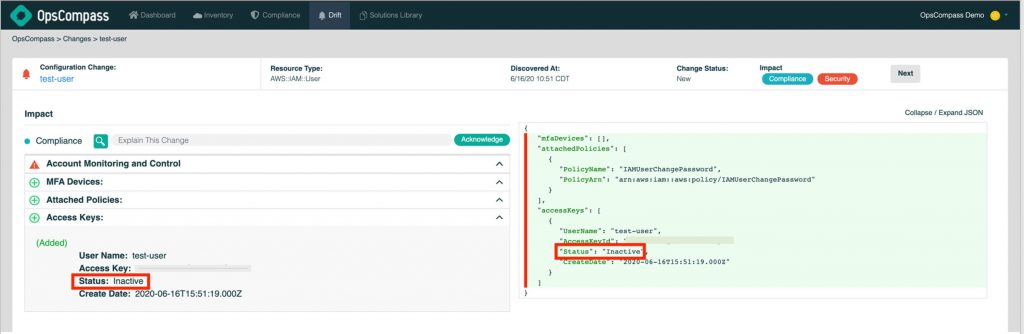
IAM Policy Drift: An inactive AWS user for 90 days was auto-disabled, potentially causing access issues.
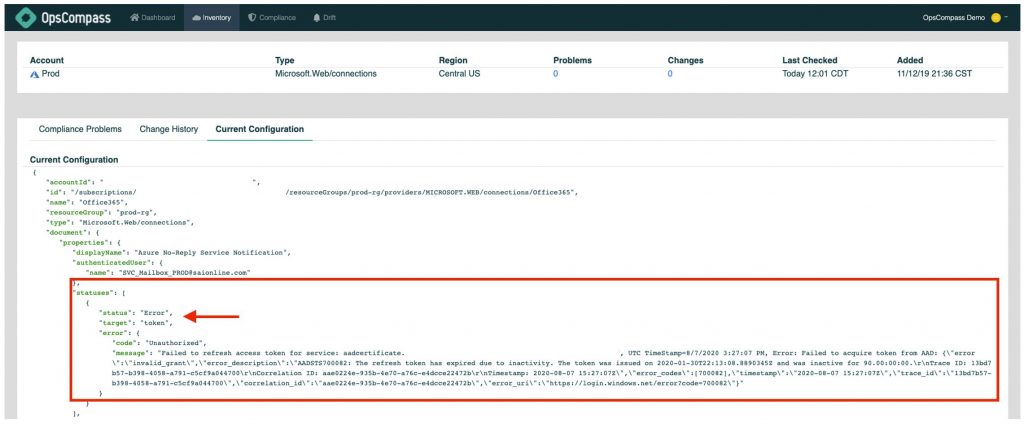
API Token Expiration: A workflow integration failed due to an expired Office 365 token.
Proactive Strategies to Prevent and Mitigate Cloud Configuration Drift
- Use continuous drift monitoring tools like Opscompass
- Enforce strict IAM policies to prevent unauthorized changes
- Automate compliance checks for security frameworks like CIS, NIST, and FedRAMP
- Implement version control for Infrastructure as Code (IaC) deployments
- Enable real-time alerts to detect and remediate drift before it causes issues
Misconfiguration: A Prefix or a Pre-Fix?
How Cloud Misconfigurations Lead to Costly Downtime and Security Risks
As cloud adoption increases, misconfigurations become more common. Unchecked drift can lead to data breaches, compliance fines, and downtime. Businesses need proactive cloud governance to avoid security gaps.
Why Cloud Security Posture Management (CSPM) is the Solution
Cloud Security Posture Management (CSPM) solutions like Opscompass continuously monitor and enforce compliance policies, reducing configuration drift risks before they escalate.
Ensuring Cloud Resilience with Opscompass Configuration Drift Monitoring
Whether securing multi-cloud environments or ensuring SaaS applications follow best security practices, Opscompass provides continuous monitoring, detecting misconfigurations and vulnerabilities in real-time.
Final Thought: Are You Concerned About Configuration Drift?
Opscompass can help. Stay ahead of misconfigurations, reduce security risks, and ensure compliance in your cloud environments.




