What does it mean to measure cloud compliance and governance?
We introduced the concept of creating scoring against our certification frameworks a couple of weeks back and it has been fascinating to watch our customers and even myself respond to this simple concept.
Customer Reaction
First, our customers back in the datacenter days, we would stuff agents on hardware and sit back and monitor the goodness of these physical objects we could get our heads wrapped around. The CPU on this box just pegged out, what is happening? Ohhh, I/O is getting crushed on this storage array, “what did the developers do this time”? SNMP trap alerted us to such-and-such device is overheating, now what?
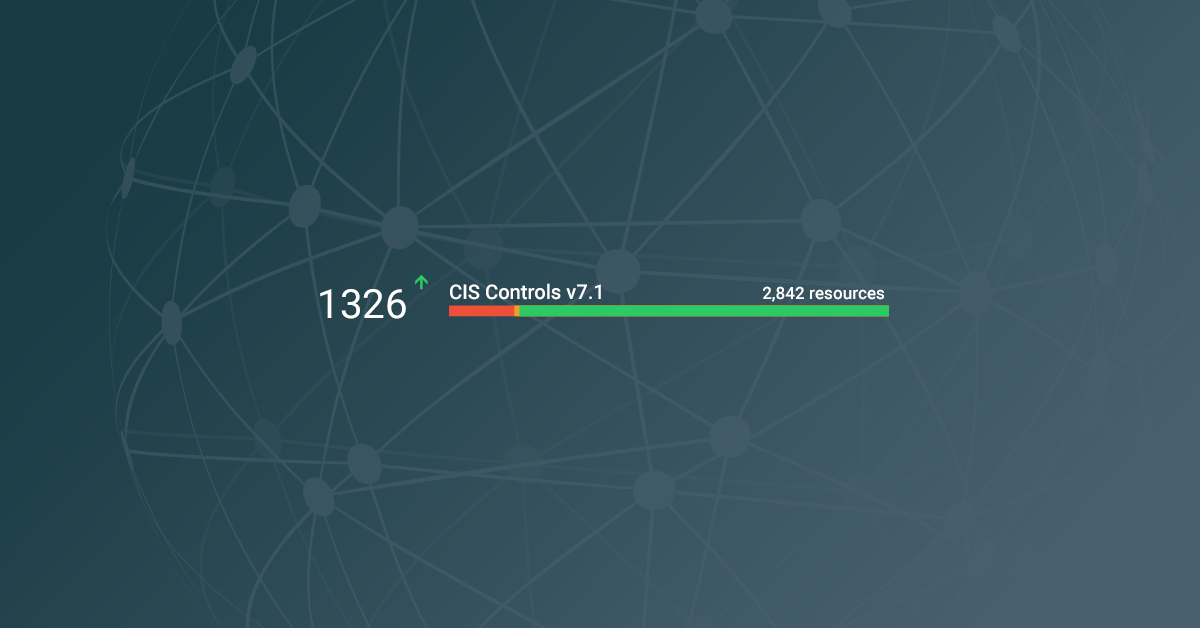
Bring us to today. I was watching our customer look at our Compliance Number for the first time. I was expecting all sorts of questions wrapped around the number, like “how did you calculate the number, your number is wrong and we did not get any of that?’ Instead what we got was, OK we knew we were out of compliance, where are the issues? Once we showed them the alerts, they went to work, the number popped quickly in the first couple of days and then it has been slowly trending up. What I have noticed is that the compliance framework has become a checklist of to-do items with feedback from the compliance number to show cause and effect. The number doesn’t have to mean anything, it just has to show two things:
- What is the scale of the change day-to-day
- Are we showing progress to a “good state”?
My suspicion is that in the process we have turned CIS and NIST certification from an auditing process to be feared, into a logical set of questions of our customer’s environments that we have pre-arranged the answers to and the customer can decide whether they like the answer. If they don’t like the answer, then go and fix it. Lastly, it also means that there is an end, no one wants to stare off into the abyss, and it is scary.
My Reaction
Now for me, I got sucked into the minutia of the number, like I said above I was expecting our customers to ask a lot of questions and I wanted to be prepared. What happened next is I got below the task list to the very subtle changes that were happening in the number. What I theorize is Azure was kicking off processes and alerting developers of compliance issues and they, as part of their normal workflow, were unwittingly helping the compliance of the environment. I don’t have the answer yet, but I suspect that we are going to be able to trap these instances and watch the patterns that the developers engage in and be able to assist them in creating better behaviors. Because at the root of all of this, we know intuitively that if all developers always created safe, secure and efficient code all of the time, then a whole security industry would collapse. Don’t worry if you are in that industry your job is secure, but we can learn more about getting there.
In this day and age of Data, this is going to be why the Public Cloud will always be better than the Data Center. We have so much more data in the Public Cloud to understand the various patterns of building applications. As a friend told me yesterday, “Party on the Data”.