Amazon’s Relational Database Service (RDS) is probably one of the most common services we see across all OpsCompass customers. When customers move databases to AWS, it’s always appealing to offload things like server management and patching by leveraging a database-as-a-service offering like RDS to realize the cloud’s efficiency promise. But when it comes to security and meeting the needs of regulatory compliance initiatives, utilizing RDS can present some challenges.
For instance, FedRAMP and other compliance frameworks call for a credentialed, or authenticated scan. This type of scan is useful because using privileged credentials allows for in-depth and comprehensive analysis of vulnerabilities. When I talk to customers and pen testers alike, I constantly hear that they can’t scan RDS because there are no hosts – it’s a cloud service after all! But this isn’t really true. Security people tend to be oriented toward discovering endpoints traditionally by nmapping a TCP/IP network, but with RDS and other AWS services, it can’t always be discovered on a VPC and there are better ways to enumerate services in use.
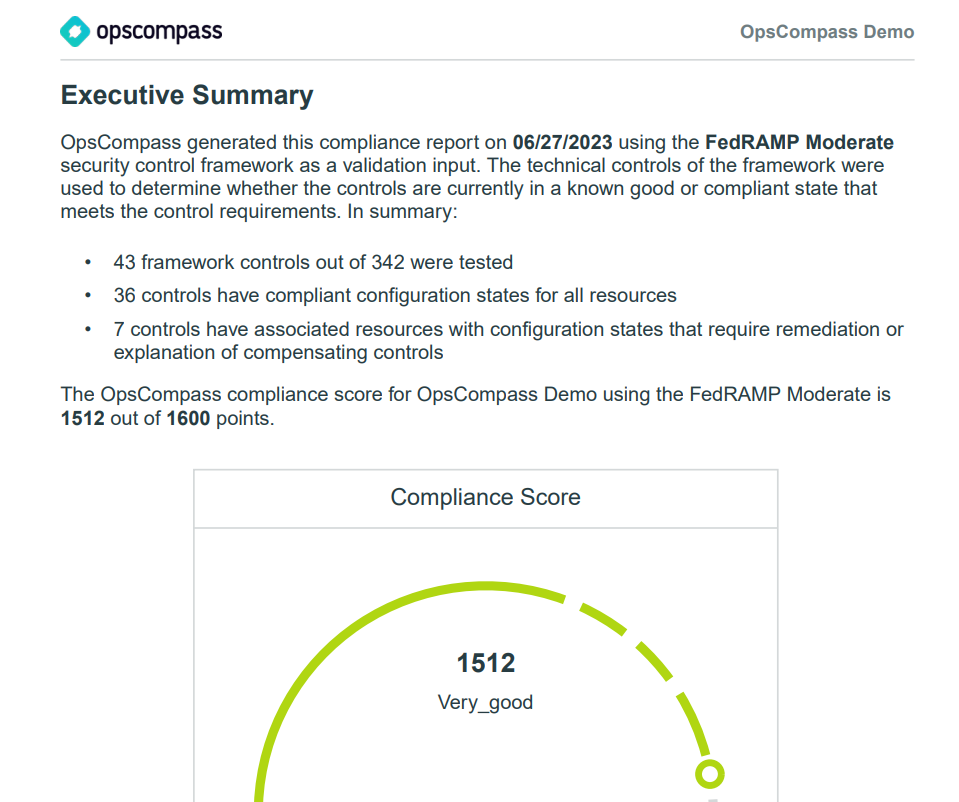
OpsCompass makes it really easy to discover new AWS resources including RDS instances and perform a credentialed/authenticated scan that will satisfy requirements like FedRAMP’s continuous monitoring period. Beyond that, customers are using OpsCompass to continuously scan all their cloud infrastructure and databases for compliance with frameworks like FedRAMP Moderate, NIST CSF, and others. In the rest of this post, I’ll show you how you can scan your AWS environment and RDS instances for FedRAMP compliance.
1. Maintain and understand your inventory
To properly secure your environment and stand up to compliance requirements it’s critical to maintain an inventory of assets. In this case, we want to have an automatically updating inventory of RDS instances and databases.
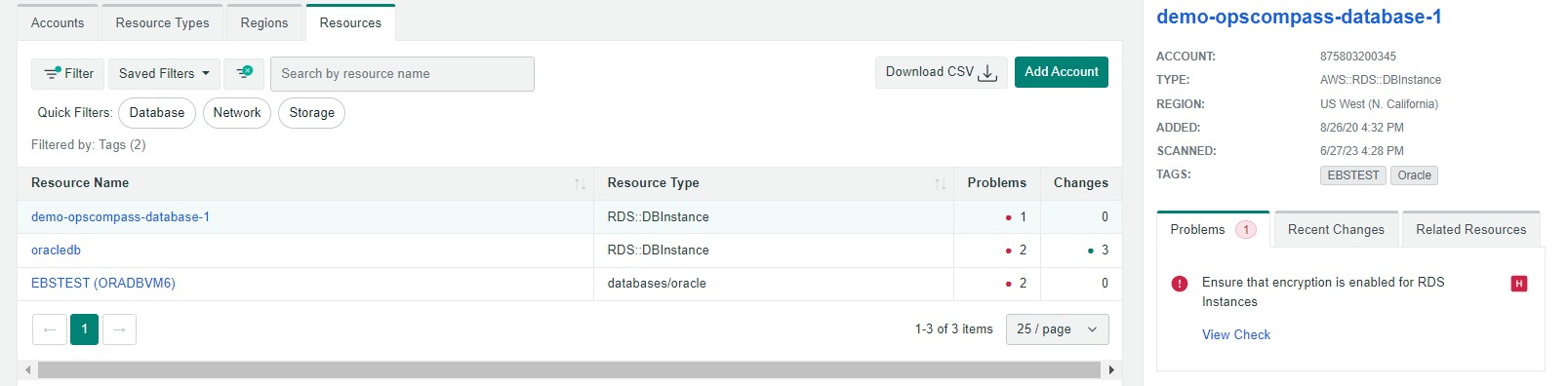
2. Continually Assess AWS infrastructure and services against FedRAMP standard
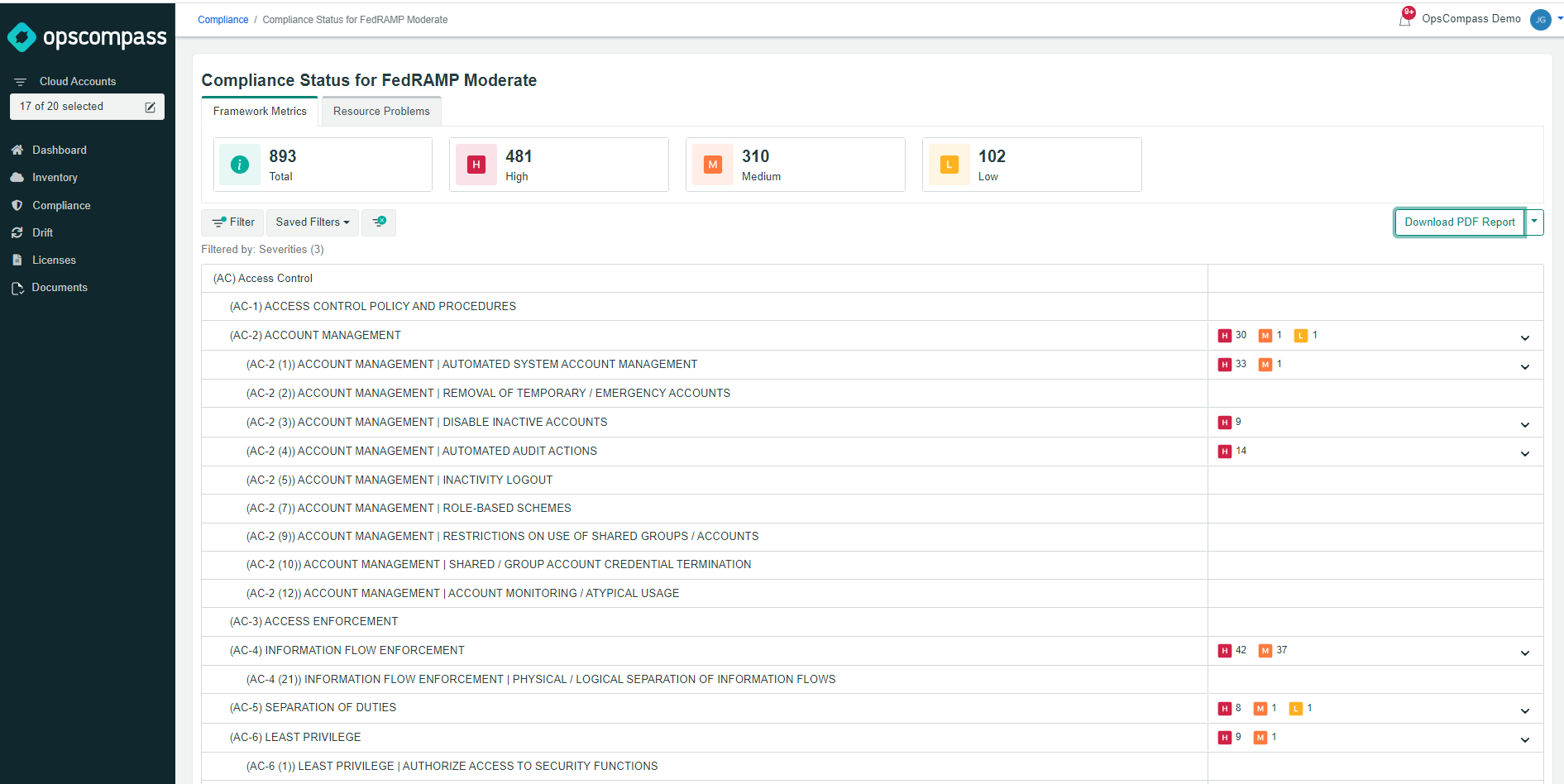
OpsCompass will continually assess your environment and check for things like solid access controls, audit and accountability, and configuration management. This whole process is automated and there are reports that can be exported via the UI and data can also be ingested via API/CLI.
3. Use OpsCompass CLI to enable data gathering scripts for the credentialed database scan
You can use the OpsCompass CLI tool to connect OpsCompass to your databases for credentialed/authenticated scanning. I also like to tag the resources in OpsCompass so I can create views oriented around this compliance initiative.
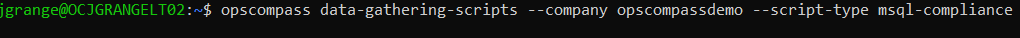
Once the data gathering scripts are successfully authenticated with the target database in the RDS instance, it will be added to your OpsCompass inventory and scanned for vulnerable configurations.
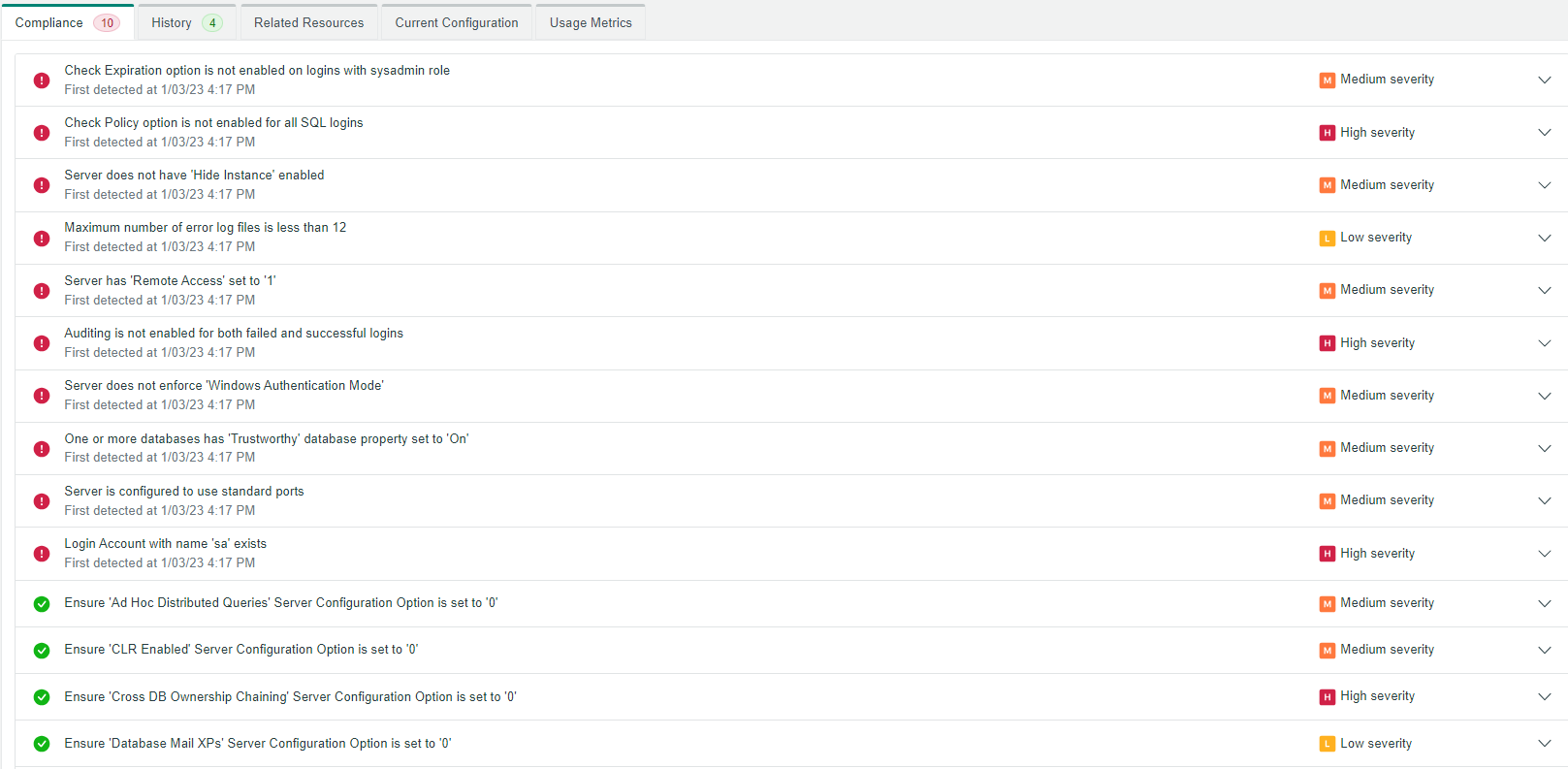
4. Review vulnerabilities and problems from the database itself, to the RDS instance, to the AWS infrastructure surrounding it.
At this point you can generate in OpsCompass a point-in-time report that provides evidence for how your AWS environment performed against each of the technical controls in the FedRAMP Moderate framework.